The first hour after a cyber incident is often referred to as the “golden hour” because this window is critical for detecting, containing, and mitigating an attack before it can cause irreversible damage. In these crucial moments, rapid identification and analysis of the threat can prevent the attacker from moving laterally or exfiltrating sensitive data. A swift response enables precise action—isolating affected systems, gathering key forensic data, and beginning the remediation process—which significantly curbs the potential escalation of the incident.
Despite the importance of this critical time frame, many companies face delays in enabling external remote Incident Response (IR) teams from gaining visibility and access. Organisational silos, overly bureaucratic approval processes, and a lack of pre-established access protocols can contribute to these delays. Often, internal IT and security teams are caught off guard, leading to a painstaking scramble as they work to provide the necessary remote visibility and access. This slow mobilisation not only hampers effective threat containment but also opens the door for attackers to further entrench themselves within the network, causing more extensive damage.
Moreover, the problem is compounded by outdated or overly restrictive IT infrastructures that were never designed with rapid external collaboration in mind. Many companies operate legacy systems that require extensive reconfiguration to allow secure remote access, often taking hours—if not days—to implement. Without a proactive incident response plan that seamlessly integrates external experts like Cyber+, organisations risk exponential losses during that critical first hour. An effective strategy hinges on regular drills, updated protocols, and pre-approved access procedures so that external IR teams can step in immediately, ensuring that swift action minimises damage, protects sensitive information, and maintains operational continuity.
Respond to emergencies more rapidly
When an incident strikes, don’t be the one casually sipping coffee while chaos unfolds. Be ready, be proactive, and take command when every second counts. Learn more about the Cyber+ approach to Cyber Incident Response reducing the reputational, operational and financial impacts.
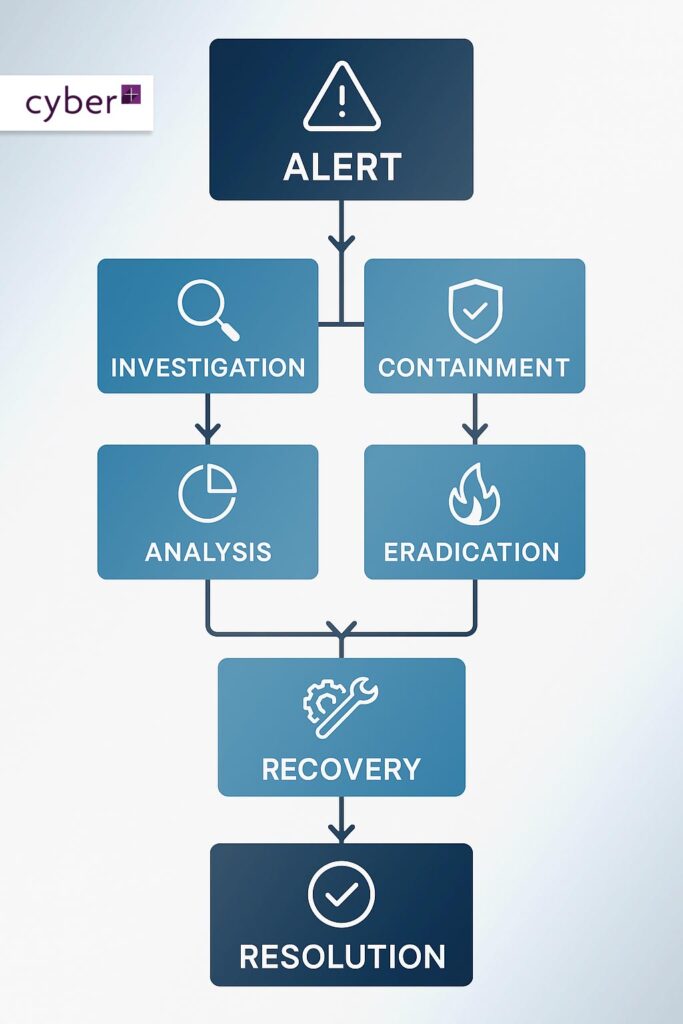

Once an alert is generated, the Cyber+ Incident Response team embarks on an initial triage to validate the threat before escalating it appropriately. Cyber+IR clients gain immediate access to cybersecurity expertise, with visual and audible insight even if the network is compromised, shaving critical hours from typical incident response scenarios.
At the heart of the process lies a critical decision point: while containment measures are implemented to prevent further intrusion, forensic teams work in parallel to collect essential evidence without delay. This twin-track approach ensures that while operations are safeguarded, the necessary technical insights are gathered for comprehensive analysis. The flow then converges for detailed incident analysis, which informs both the immediate remediation actions and the necessary communication with stakeholders. Finally, after remediation, recovery, and a thorough post-incident review, the process culminates in a formal closure of the incident. This structured yet parallel approach is vital for minimising impact and shortening response times in the rapidly evolving world of cybersecurity.
Are you ready to explore how CyberPlus can help your organisation with Cyber Incident Response Management? Are you truly prepared for a security breach? When incidents strike, seconds matter. Just like we’ve fortified major organisations, we offer comprehensive white-hat testing, strategic incident response evaluations, tailored training, and immediate support when you need it most. Your defence starts with proactive readiness—because the first hour can make all the difference. Contact us today to discover more.

